Security at PushMetrics
What we do to keep your data safe.
We understand how important the responsibility of safeguarding data is to our customers. The security and privacy of your data are fundamental to the success of both you and us, and this is why we make protecting it a top priority.
We’re committed to being transparent about our security practices and helping you understand our approach. Therefore, we aim to be as clear and open as we can about the way we handle security.
This document provides an overview about our approach to security, availability, processing integrity, confidentiality, and privacy.
If you have further questions, don't hesitate to contact us.
Infrastructure Security
Production System
The PushMetrics production environment is hosted at Amazon Web Services (AWS), one of the industry-leading service providers, on servers based in the EU (eu-central-1, Frankfurt). Customer data is processed by and stored in AWS EC2 instances and S3. Development occurs on systems in environments that are separate from the production environment.
Amazon AWS maintains multiple certifications for its data centers, including ISO 27001 compliance, PCI Certification, and SOC reports. For more information about their certification and compliance, please visit the AWS Security website and the AWS Compliance website.
Strong internal authentication and access controls are implemented to restrict administrative access to our production systems, internal support tools, and customer data. All administrative access to our production systems requires two-factor authentication. Machine-level access restriction relies on a key-based authentication and uses transport encryption to enhance data confidentiality in transit. All data traffic is encrypted to and from PushMetrics production systems.
Network Protection
PushMetrics Services run in an access-restricted Virtual Private Cloud (VPC) provided by AWS. All external-facing traffic is routed through proxy servers for which firewalls are configured according to industry best practices; unnecessary ports are blocked by configuration with AWS Security Groups.
In addition to system monitoring and logging, we have implemented two-factor authentication for all servers access across our production environment.
Third-Party Vendors
Sensitive data, such as data from Tableau or credentials are never stored outside of our proprietary services hosted on Amazon AWS. Customer information (such as such as names, email adresses, messages you send us) is also processed and stored in cloud-based systems provided by third parties.
We vet our vendors carefully, make sure they are safeguarding data properly and review their security and privacy guidelines frequently.
For example, we make sure vendors comply with the EU’s GDPR legislation, follow Cloud Security Alliance (CSA) best practices or publish SOC reports.
PushMetrics currently processes and stores customer information with providers that can be found in this list. Please refer to their respective security policy for further details.
Data Security
Data in transit
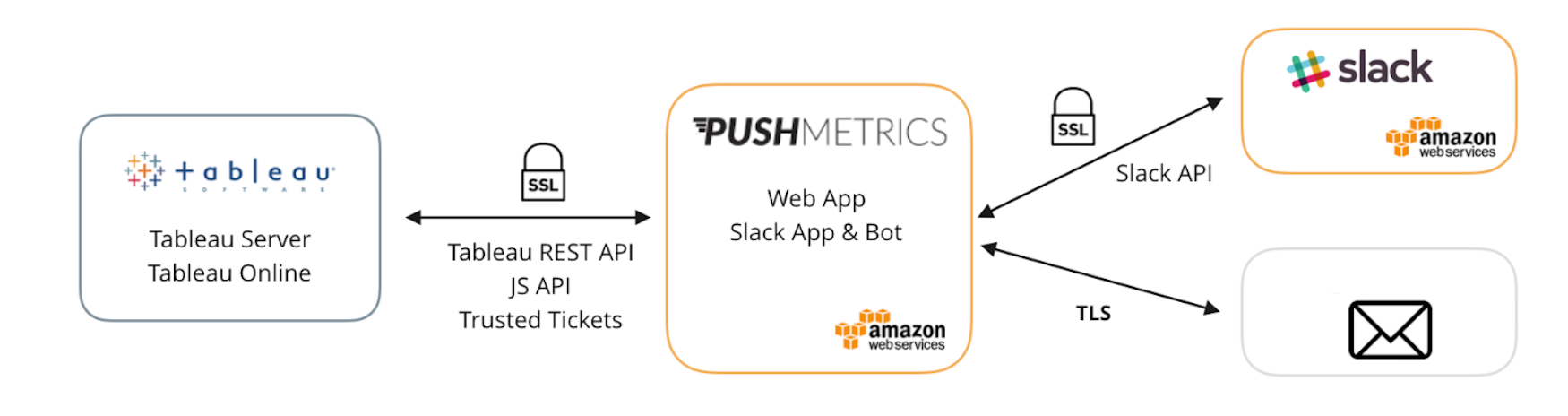
PushMetrics transmits data over public networks using SSL encryption. This includes data transmitted between all external parties, especially Slack and Tableau, and the PushMetrics service. PushMetrics supports the latest recommended standards to encrypt all traffic in transit, including use of TLS protocols and SHA256 with RSA encryption.
Data Transmission between PushMetrics, Tableau and Slack
The PushMetrics services utilize a range of APIs provided by Tableau Software and Slack, including the Tableau JavaScript API, the Tableau REST API and the Slack API. Authentication to all APIs used is strictly key-based and all traffic is always SSL encrypted. System-generated emails are TLS encrypted by default.
Data at Rest
Data at rest in the PushMetrics production network is encrypted using FIPS 140-2 compliant encryption standards. This applies to all types of data at rest within our databases, file stores, database backups, etc.
Data retrieved and stored from Tableau
Upon establishing a connection between PushMetrics and your Tableau instance, PushMetrics retrieves and stores meta information regarding your Tableau environment and meta information about the contents stored in it, such as server version, workbook names, view names or thumbnails of views. User-requested file exports (via ad-hoc request or through scheduled reports) of Tableau Views (as of today PNG, PDF, CSV or XLS files) are generated on the customer's Tableau instance and then transferred to our servers using an SSL-encrypted connection. Retrieved files are stored in AWS S3 and encrypted at rest and will be deleted once no longer needed. We will never request file exports from Tableau without you triggering it or your explicit permission to do so.
Data Retrieved and Stored from Slack
Upon adding the PushMetrics Slack App to your Slack team, PushMetrics retrieves and stores your team's user information such as names, email addresses and profile information as well names of public and private channels. This information is required by our application to provide the functionality of our services. For example, we retrieve the names of all channels and users in order to provide them as recipient options when scheduling a report. We will never use provided information about your team members to contact them without your explicit permission unless they sign up themselves and hence authorize us to do so.
Payment Information
All our website financial transactions are handled through our payment services provider, Stripe. You can review the provider's privacy policy. We will share information with our payment services provider only to the extent necessary for the purposes of processing payments you make via our website, refunding such payments and dealing with complaints and queries relating to such payments and refunds.
Product Security
Role-based Access
PushMetrics supports hierarchical group access controls and a set of different user roles to enable different access levels for users of one organization.
Authentication
PushMetrics supports oAuth 2.0 authentication via Slack to authenticate users in your without requiring to enter additional login credentials. For password based authentication, a strong password is enforced following industry best practices.
Passwords & Credentials
Your password, Slack tokens and Tableau credentials are encrypted and never stored in our database in a readable/unencrypted format. You are responsible for choosing a strong password and keeping it secret. PushMetrics encourages the usage of a password manager.
Availability
We understand that you rely on our services. We're committed to making PushMetrics a highly-available service that you can count on. Our infrastructure runs on systems that are fault tolerant, for failures of individual servers or even entire data centers. Our team tests disaster-recovery measures regularly and staffs an around-the-clock on-call team to quickly resolve unexpected incidents.
Customer data is stored redundantly at multiple locations in our hosting provider’s data centers, capable of high availability and automatic failover to ensure availability. We have backup and restoration procedures, which allow recovery from a major disaster. Customer data and our source code are automatically backed up nightly. The on-call team is alerted in case of a failure with this system. Backups are fully tested regularly to confirm that our processes and tools work as expected.
Status Page
The current availabilty of all PushMetrics services can be checked on our status page under https://status.pushmetrics.io. In case of major outages or longer periods of scheduled maintenance, we will reach out to our customers proactively.
Confidentiality & Employee Access
We place strict controls over our employees’ access to the data you and your users make available via the PushMetrics services and are committed to ensuring that customer data is not seen by anyone who should not have access to it. The operation of the PushMetrics services requires that some, selected and qualified employees have access to the systems which store and process customer data. For example, in order to diagnose a problem you are having with the services, we may need to access your customer data. Every access is being logged in our system and these employees are prohibited from using these permissions to view customer data unless it is necessary to do so.
All our employees and contract personnel are bound to our policies regarding customer data, operate under NDAs, and we treat these issues as matters of the highest importance within our company. We enforce screen lockouts and the usage of full disk encryption for company laptops. Please also refer to our privacy policy for further information.
All members of our team go through a basic, role-specific training with respect to security awareness and every team member is required to acknowledge and sign a data privacy declaration informing about obligations according to current legislation.
Other Security Topics
Optional Security Features
We're committed to fulfilling custom security requirements and offer additional layers of security on request.
Some of these include:
- Trusted Authentication to Tableau - alternative authentication method, available for Tableau Server only.
- Custom data retention policy can be set by the user to a minimum of 1 day and a maximum of 365 days.
- Dedicated private data storage (AWS S3) in a separate security group (e.g. only accessible inside your network)
- Fully separated server instances for your account in either our or your AWS environment
- Full on-premise deployments
Ongoing Efforts
All new features, functionality, and product changes go through a security review process. In addition, our code is tested and manually peer-reviewed prior to being deployed to production.
In addition to our existing procedures in place, we commit to implement further measures going forward, including external compliance certifications.
Responsible Vulnerability Disclosure
If you are a security expert or researcher and you believe that you have found a vulnerability in PushMetrics, we encourage you to notify us at security@pushmetrics.io.
Please make an effort in good faith to protect our users' privacy and data. We look forward to working with you to resolve the issue as soon as possible and will award bug bounties if applicable.
Conclusion
We take security seriously at PushMetrics because every person and team using our service expects their data to be secure and confidential. Safeguarding this data is a critical responsibility we have to our customers, and we work hard to maintain that trust.
Last updated: August 24, 2020